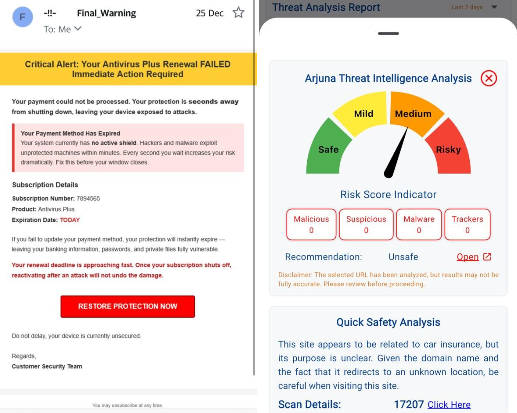
This Is How Phishing Looks in Real Life — And Why Real-Time Protection Matters More Than Ever
Phishing scams have evolved. They are no longer easy to spot emails filled with spelling mistakes or suspicious formatting. Today’s phishing attacks are polished, urgent, and designed to exploit human psychology in seconds. A recent real-life example highlights just how convincing these scams have become — and why relying on “being careful” is no longer enough. A Common Morning, A Dangerous Email The email looked urgent. It claimed that an “Antivirus Plus renewal FAILED” and warned that device protection was “seconds away from shutting down.” The message was carefully crafted to trigger fear and immediate action. It included: At first glance, it appeared legitimate. And that is exactly why phishing works. Why Modern Phishing Is So Effective It Uses Psychology, Not Poor Design Phishing today isn’t about obvious mistakes. It’s about pressure, timing, and emotional manipulation. Scammers know that fear reduces rational thinking. When users feel rushed, they are far more likely to click without verifying. It Mimics Trusted Brands and Services From antivirus renewals to bank alerts and delivery updates, phishing emails often impersonate services people already trust. This familiarity lowers suspicion and increases the chance of interaction. The First Click Is Where the Damage Happens Most cyber damage occurs the moment a malicious link is clicked. That single action can lead to credential theft, malware installation, financial loss, or identity compromise. How Real-Time Protection Changes the Outcome Before there was even time to react, Arjuna flagged the link as unsafe and displayed a clear risk warning. Instead of panic, there was clarity. This is the power of real-time protection: Security should not depend on users always making perfect decisions under pressure. It should intervene at the exact moment of risk. Why “Be Careful” Is No Longer a Strategy Telling users to “be careful” assumes unlimited attention, technical knowledge, and emotional control. In reality, people are busy, distracted, and human. Effective cybersecurity must: Protection should support users, not test them. How to Recognize Phishing Attempts If an email or message: Pause. Verify. Do not react under pressure. Legitimate organizations do not force instant decisions through fear. Real Threats Don’t Wait — And Protection Shouldn’t Either Phishing attacks are becoming faster, smarter, and more convincing. The window between receiving a message and making a mistake is often just seconds. That is why real-time protection is no longer optional. It is essential. With proactive threat detection and instant risk alerts, users can move through the digital world with confidence instead of caution. Because when threats act instantly, protection must do the same. Download Now!