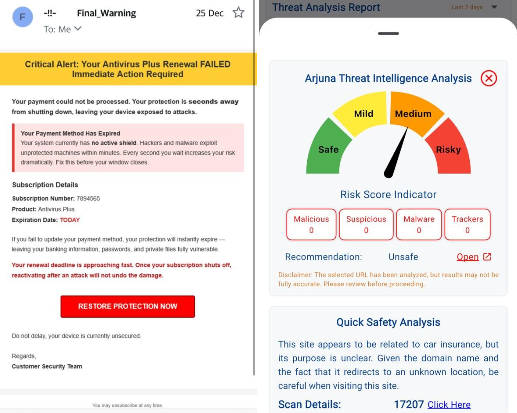
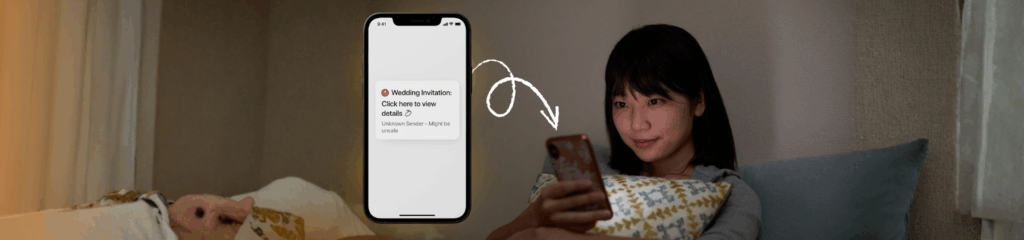
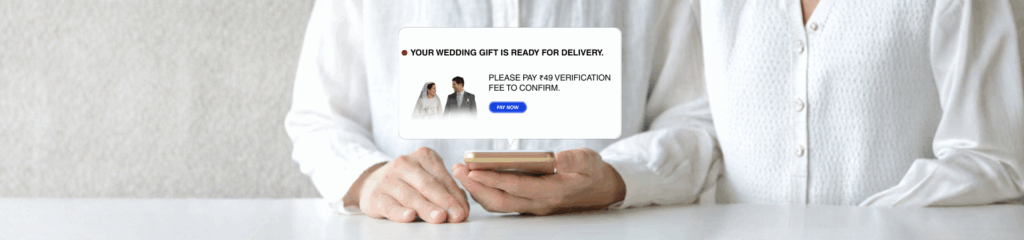
AI is a superpower, but like any powerful tool, it can be used for good or bad. Cybersecurity experts are now sounding the alarm about a rising form of AI-driven crime called “vibe hacking” (also described as an evolution of AI-enabled attacks). These attacks automate and scale harmful activity, from drafting ultra-convincing phishing messages to orchestrating personalized extortion, and they’re becoming cheaper and easier to buy on dark-web marketplaces. Source: Economic Times Below I’ll explain what vibe hacking is, why it’s different (and scarier) than older scams, and most importantly, practical steps you can take today to protect your digital life. I’ll also show where intelligent mobile protection like Arjuna — The Cyber Shield can help, without the tech jargon. What Exactly Is Vibe Hacking? “Vibe hacking” describes how criminals are using generative AI models and agentic AI tools to automate the whole attack lifecycle. Imagine a toolkit that writes believable phishing emails, builds malicious code, identifies vulnerable targets, and even chooses which files to steal, all with minimal human input. Researchers and industry leaders warn that these tools can be purchased for surprisingly low prices and can bypass legacy safety systems. Source: Economic Times A few worrying examples called out by experts include AI coding assistants being exploited to steal data from organizations and “Evil LLMs” like FraudGPT and WormGPT being used to craft polymorphic malware, deepfakes, and tailored social-engineering campaigns. Source: Economic Times Put simply, attackers can now scale campaigns that used to require teams of skilled hackers, and they do it much faster and cheaper. Why This Is a Turning Point There are three reasons vibe hacking is different from the phishing and malware we’ve seen before: That combination, fast, convincing, and cheap, is exactly what makes vibe hacking so dangerous. It widens the attacker pool and makes large, automated scams much more likely. What These Attacks Look Like in the Wild Vibe hacking can show up as hyper-personalized phishing emails that reference your recent purchases, colleagues, or calendar events; deepfake voice calls asking for verification codes or confirming sensitive transactions; malicious agents that crawl shared documents and automatically inject poisoned prompts or hidden instructions; or rapid ransomware campaigns where AI automates reconnaissance, payload creation, and distribution. Because these attacks can be so tailored, the usual “look for spelling mistakes” advice isn’t enough anymore. How to Protect Yourself – Practical and Simple You don’t need to be an expert to reduce your risk. Here are effective, everyday steps: And a critical step many people skip: use a proactive mobile security tool that scans links and risky behaviour in real time. Where Arjuna Fits – Protection That Actually Helps Awareness is necessary, but it’s not sufficient against vibe hacking’s speed and scale. That’s where Arjuna — The Cyber Shield comes in. Arjuna provides real-time scanning of links, messages, and app behaviour so threats are identified before they can act on your device. When AI-driven campaigns attempt to deliver malicious links, deepfake payloads, or convincing phishing pages, Arjuna raises an immediate alert, blocking unsafe interactions and preventing automatic downloads or credential capture. In practice, that means you don’t have to recognize every sophisticated scam yourself; Arjuna’s detection layer does the heavy lifting, giving you time to verify and act calmly. A Few Extra Tips for Teams and Organizations If you manage a small business or a team, consider these extra steps: train staff on AI-amplified social engineering (use simulated phishing that mirrors modern, targeted techniques); review access to sensitive systems and rotate credentials, especially for APIs and shared repositories; monitor for “tool poisoning” risks to ensure internal models do not ingest untrusted data that could contain malicious prompts; and work with vendors to ensure their AI products include safety testing and red-teaming. Final Thought Vibe hacking is a wake-up call: AI has made cybercrime cheaper, faster, and far more convincing. But the solution isn’t to panic; it’s to adapt. By combining cautious habits (pause, verify, update) with layered protection, including intelligent tools like Arjuna — The Cyber Shield, you can reduce exposure and stay one step ahead of automated attacks. If you want to take immediate action, start with two things today: enable MFA on your critical accounts and install a real-time mobile security app that scans links and risky app behaviour. The future of cybercrime is automated; your defense should be too.